The cyber-attack on CCTV cameras and other IoT devices, is a very big risk that organizations face today, since the privacy, security, and compliances of the organizations and critical infrastructure institutions. Redinent Innovations, XIoT platform helps organizations to protect CCTVs and any other cyber physical devices, such as Access Controls readers, Energy meters, Smart lights, EV charging stations etc., against any cyber-attack on these devices by detecting vulnerabilities and helping them fix those vulnerabilities.
REDINENT IoT THREAT SCANNER
Redinent IoT Threat Scanner automatically discovers IoT and embedded devices, finds vulnerabilities and common weaknesses at scale. After the assessment, Redinent users receive a detailed report of the findings that includes an overview of the IoT devices, vulnerabilities, weaknesses, risks, and threats the platform found while running in the user’s environment.
IoT ASSET INVENTORY AND CLASSIFICATION
The Redinent platform discovers and classifies every IoT and unmanaged device in the user’s environment, including but not limited to Smart IP Cameras, Smart Solar Panels, Smart HVAC Systems, Wi-Fi Routers, Smart Motion Sensors, Smart Water Meters, Smart TVs, Smart Speakers, Wi-Fi Printers, Smart Smoke Detectors/Smart Fire Alarms, Smart Conferencing, Smart EV Charging Stations, Smart Lights, Smart Access Card/Control, Smart Gas/Utility Sensors, Smart Elevator Control, Smart Thermostats, Smart Meters, Smart Switches, Smart Homes, and many more.
RISK AND THREAT ASSESSMENT
After identifying a device, the Redinent platform calculates the asset’s risk score based on factors, including:
- Risks originating from unpatched firmware versions or known hardware exploits.
- Risks originating from human error and configurational weaknesses.
- Risks originating from OEM themselves including obscure white- labelling and underlying firmware detections.
DEEP & EXHAUSTIVE
- Scan IoT Devices to provide security teams with visibility into vulnerabilities.
- Monitor trends across various scans through customizable dashboards.
- Minimize network impact, optimize security and compliance assessments, and unify reporting through a single assessment for vulnerabilities, configurations, controls, and policy checks.
- Receive in-house step-by-step instructions from Redinent experts to remediate risks.
- Eliminate a traditional blind spot for security teams and stay complaint with privacy regulations.
Redinent – IoT Threat Assessment Modules
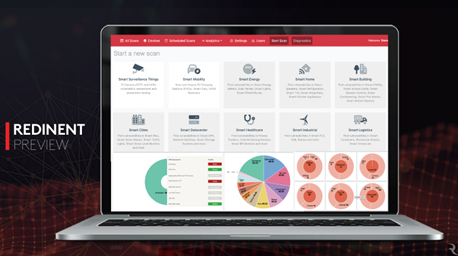
Proven in various infrastructures Redinent delivers the following core capabilities
Fast Unified Secure compliance
Minimize network impact, optimize security and compliance assessments, and unify reporting through a single assessment for vulnerabilities, configurations, controls, and policy checks.
Discover vulnerabilities like an attacker
Redinent expert scanning system emulates techniques used by human hackers to build upon knowledge from prior exploits and identify additional vulnerabilities, resulting in a more complete risk assessment.
Vulnerability validation with Evidence
Redinent not only finds vulnerabilities but captures and records evidence to validate risk.
Powerful Risk and Data Analytics
Redinent provides built-in and fully customizable report templates to create reports for everyone.
Compliance
Redinent enables organizations to stay compliant with ISO 27001 and COBIT standards for risk, vulnerability, and configuration management requirements.
Redinent benefits compared to modern IoT Security Platforms
| Modern IoT Security Platforms | Redinent | |
| SCAN TYPE | Tests are run on network traffic generated from the the IoT device. | Tests are run directly on IOT devices. |
| COVERAGE | Tests are run only for the white labeled company. | Tests are run for the original OEM detected by Redinent. |
| ACCURACY | Prone to false positives. | Zero False Positives, Exploit and intrusion based. |
| ANALYSIS | Traditional Analysis. | Innovative IoT Vulnerability Discovery Algorithms. |
| RESEARCH | Zero Days not a priority. | Zero Days are integral part of Redinent. |
